Authorisation – It Shows You Care.
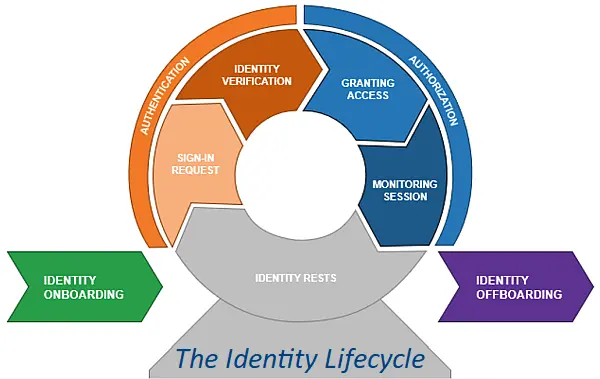
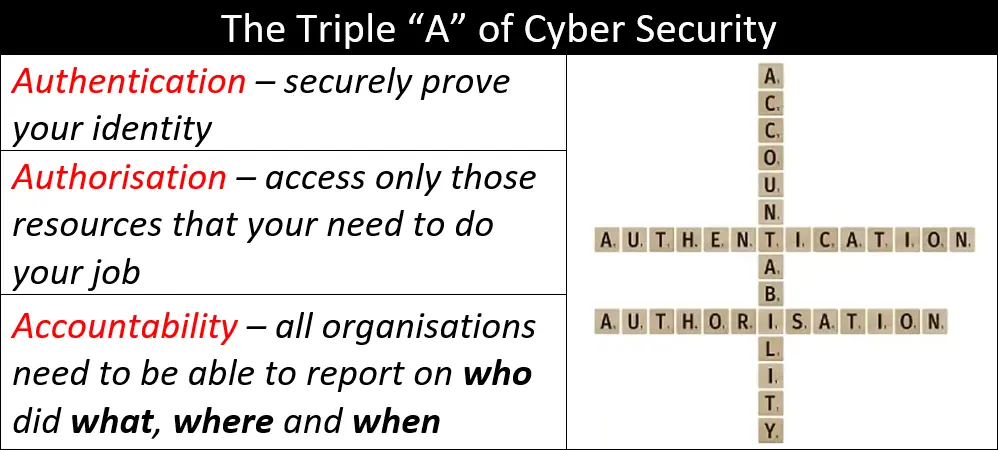
Authentication, Authorisation and Accountability. This is the second part of a three-part series looking at the basics of the cyber security principle of “AAA”.
Once logged in Authorisation is king.
Once a user has proved their identity to the system their credentials should then give them access to only those resources they need to do their job and no more. This is often referred to as “the principle of least privilege” and it is a good place to start if you are trying to secure your information.
Authorisation by RBAC or ABAC
We are going to be using Role Based Access Control (RBAC) here – access based on the user’s role. However, I wanted to mention the other way of determining access, Attribute Based Access Control (ABAC) – access is granted to resources based on attributes of the subject, object, environment, and policy. ABAC allows for fine-grained and dynamic access control but is more involved. RBAC is more straightforward to understand and implement.
Authorisation = Information Segmentation
You need two things now to get started – but it will soon get more complicated!
- A list of your team members and the roles they perform.
- Remember some people have several roles and they may need different credentials to meet each set of responsibilities.
- Importantly this means any administrator account (for anything) should not be used for day-to-day working.
- Here is a real world example where two accounts with different levels of authorisation are needed.
Are you using Bring Your Own Device – BYOD – to save money?
- A list of resources that need managing.
- In SharePoint this means a folder structure to organise and manage. Once you start on this task you will probably find you need to move information around to comply with your new security standard.
- Other resources should be treated in the same way. This includes accounts software, your marketing tools, production software, website access for content production, door controls… You can make your own list.
From there you join the dots up and start to grant authorisation to the resources based on all the user roles.
The Cyber Security Advantage
We are all aware of encryption ransomware – a good backup helps defend against this type of cyber-attack, and the threat actors know it. So they have been changing their focus to data theft rather than encryption – they then attempt to extort money from you or they will release your sensitive information to the public.
When you have your information segmented, it can limit your exposure if the hackers only have credentials for a subset of your information rather than all of it.
Authorisation also helps defend against the insider threat, again limiting your exposure to a subset of your information.
A real time, 24/7/365 defence is required for both of these types of attacks. Information segmentation means that the sensitive information you have can be monitored and if threat-type activity is spotted immediate action can be taken. (Our enhanced 24/7 continuous monitoring is launching very soon – contact us for details to be an early adopter or watch this space for details in August.)
Authorisation – a Conclusion
Always remember the principle of least privilege.
Next…
Why do all of this?
Accountability!
Clive Catton MSc (Cyber Security) – by-line and other articles
The Series
Part 1 Authentication – Who Do You Let In?
Part 3 Accountability – It Shows You are Watching.
Further Reading
Authentication – Who do you let in? (Part 1 of the Series)


