Risk. Where do you start?

I have recently written a couple of articles looking at risk, one on code and one on WordPress. These led to a discussion with a client who wanted me to report on their organisation but for budget reasons wanted to restrain the scope of the report.
So I took them – and you – back to the start.
You cannot eliminate all risk
You cannot eliminate all risks – that is just a fact. A real fact, not a “politician fact”, that I have made up so you will buy (vote) from me.
What you have to do is manage your risk. Find the risks that you are going to do something about and find those that you will have to live with. Although remember that today’s answers to that statement may be different in a year’s time when you review this process.
Start the Conversation
What you have to understand is what your organisation wants to achieve and create a cyber security plan that supports those goals and does not prevent you from achieving them. However, the plan may interfere with how you achieve them to reduce your risks.
So start with these questions:
- What are we trying to achieve? Include thinking about your reputation.
- What needs to be protected? What are the critical areas of our organisation?
- Where is our sensitive data?
- What are our critical resources? Include communications and your people here.
- What do we not want to happen? Ransomware, loss of production, leak of our IP data, getting into the press for the wrong reasons, etc..
Remember as you go through this there may be external constraints on your decisions, such as regulations, governing bodies, compliance, contracts, etc.. During the start of the conversation do not let budget be a restraint – aim for the stars. It may not be in this round of spending but if you know you want it, it can be in next year’s budget.
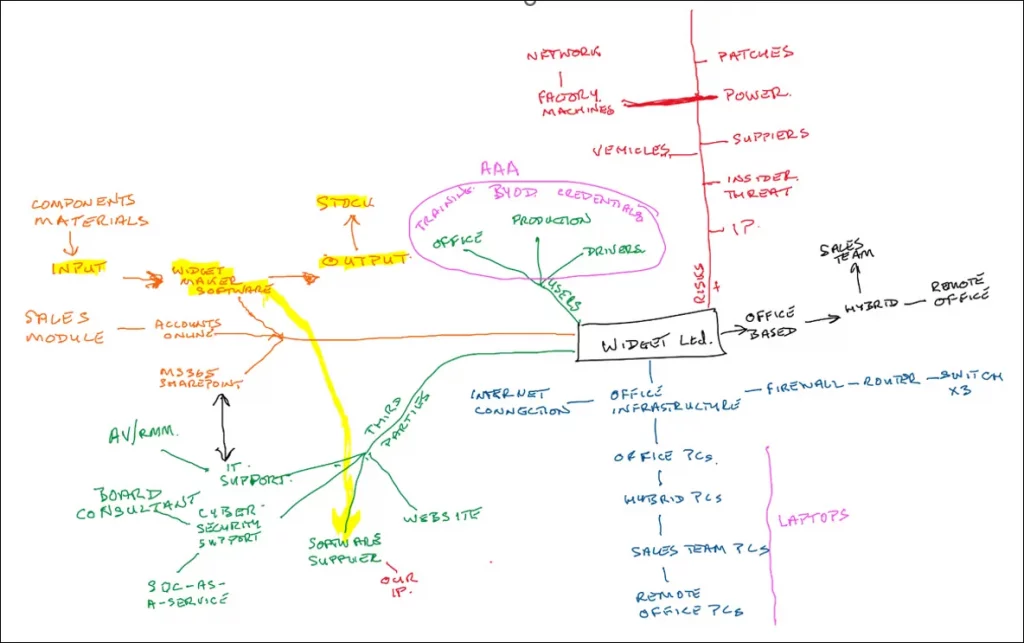
It is time to get the whiteboard out!
Who starts The Risk conversation?
It has to be a senior member of your team and it needs board level support – because some of the answers you may come up with, will not be palatable.
The conversation may (should) be driven by the board who should pose specific questions for the risk task force to solve.
For instance:
- Is our current cyber security fit for purpose? (obviously)
- What are the current threats and our risk from them? If email phishing is not included in the answer to the above question – then this is a quick positive hit for the committee – get some cyber security awareness training for all of your team that includes social engineering and phishing attacks.
- What parts of our organisation need special protection?
- If we suffer a cyber attack, will we end up in the national press because of what we do or what we could potentially leak?
- And so on…
These concerns and questions will help the task force write their report.
But this only takes you to sitting around the table, on the first morning, with the tea, coffee, and croissants untouched. But it is a good start.
Next…
I will take Step 2.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Griffor, E. (Ed.). (2016). Handbook of system safety and security: cyber risk and risk management, cyber security, threat analysis, functional safety, software systems, and cyber physical systems. Syngress.
Further Reading
Featured photo by Skitterphoto
Whiteboard image clivecatton.co.uk


