Prioritise Risks and Propose Risk Management Actions

This is the final part of our introduction to risk management, and first you should review and prioritise risks you identified earlier, then implement risk management strategies.
Risk get it written down
Strategies include implementing cybersecurity controls, halting risky activities, transferring the risk through insurance, or accepting the risk with the associated consequences.
For risks requiring controls, consider using established standards (e.g. Cyber Essentials) as a control baseline, and make sure you have confidence in the security controls by carrying out assurance activities. These activities should work together and be logical and must be systemised to ensure they meet the brief and encourage staff to implement them in accordance with an agreed timetable. Address each risk, each treatment, and each assurance methodology – to do this we recommend creating a table as shown below:
An Example of a Risk Analysis Plan
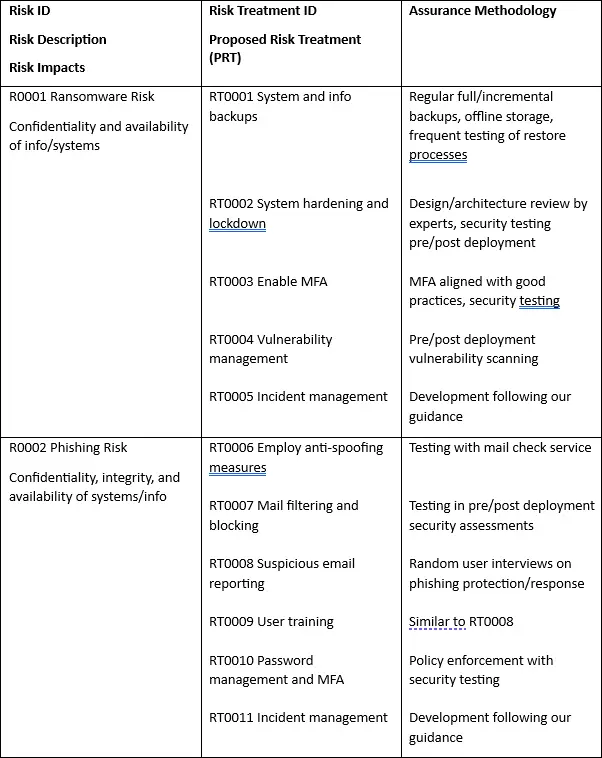
Risk assessment and management must be viewed as an ongoing process and reviewed regularly to adapt to evolving threats and technologies. This will ensure effective cybersecurity.
Risk – A Conclusion
This mini-series was never going to be a complete course in risk management. Clive got you excited about the cyber security side of risk at the beginning. He then passed the series on to me to give you a flavour of the business side of a risk project.
What we hope is that you are now thinking about the risks associated with all aspects of your operation.
If you think you need help or would like to chat to me online about anything in this mini-series get in contact via the contact page.
Diana Catton MBA – by-line and other articles
Photo by Christina Morillo


