Code Risk
Code risk is a follow-on to my article on WordPress risk and it neatly merges into my article on elephants. Both of which you should have a look at, before continuing.
So you have your own custom application that your organisation depends on, one hundred percent. Let’s look at some of the business risks that could be associated with that business decision.
Once upon a time you would have had your own server running the application – that could still be the case but it is more likely now that you have a web app or app associated with your website. This article works for any type of custom code, where you are the sole user and there is no user base driving support, security and patches.
Where is the Code Risk on my Diagram?
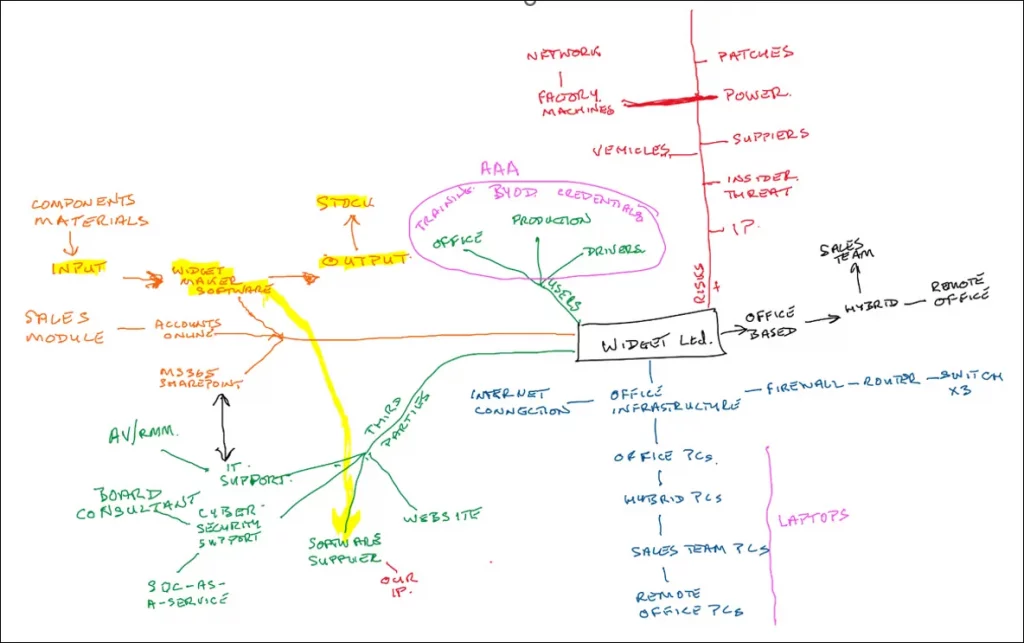
Below is the diagram from my elephant article – created as a starting point to visualise the organisation and show up the risks and vulnerabilities. In it, the code risk for the company application is orange with a highlighted link to an independent developer you got to do the job.
What questions should you ask?
From the diagram it is obvious that Widget Ltd would come to a halt if the Widget Maker Software had a flaw, so what can you do about that?
The very first thing…
At the very start of the project you need to appoint a senior member of your management or board to have responsibility for the software package. Make it their primary job – it is that important.
That person can then bring all the stakeholders together and ensure that the cyber security, IT and operations teams within the business are talking to the vendor. It will also show the vendor you are serious about their software.
Back to the questions…
In no particular order:
Externally
- Does the vendor use a software repository for code snippets or version management? Code repositories are key targets for cyber criminals. (Software Repositories)
- Does the vendor have a process in place to check for cyber security vulnerabilities in their code?
- Is there a management process for the user with access to edit the code?
- Are there back-ups and the ability to wind the code back to a good version?
Internally
- What is the procedure for deploying code onto the production system? Is it tested internally before commitment?
- Is the production network secured?
- Is the internet connection to the production network as secure as possible?
- What monitoring is in place?
- What is the AAA scheme and management process for users?
Code risk, a sort of conclusion
This is not a complete list – it is here to get you thinking about the cyber security code risk and how by managing that it will reflect well on the business activities that make you money.
Clive Catton MSc (Cyber Security) – by-line and other articles
p.s. Not sure what AAA is? That is the subject of another of my articles next week.
Further Reading
Risk Analysis – How to eat a very large quadruped!
Photo by Markus Spiske


